Table of Contents
- What to Consider When Evaluating Key Vault Security
- A Comprehensive Guide to Implementing Azure Key Vault
- A Deep Dive into the Security Features of Azure Key Vault
- Best Practices for Securing Your Data with Azure Key Vault
Azure Key Vault is a cloud-based service that provides secure storage and management for keys, secrets, and certificates used for protecting data and applications. With Azure Key Vault, users can securely store and control access to cryptographic keys and other secrets used in cloud applications and services. In this article, we will discuss the security features of Azure Key Vault and how it can help keep your data and applications secure.
Exploring the Security Benefits of Azure Key Vault
Azure Key Vault is a cloud-based service offered by Microsoft Azure that provides secure storage for application secrets, such as passwords, API keys, certificates, and connection strings. It is designed to protect sensitive data from malicious actors by providing a secure central repository for key management. Key Vault helps organizations protect their data from unauthorized access, reduce costs associated with managing keys, and ensure compliance with security standards. Key Vault provides a variety of security features to protect data, including encryption, authentication, and authorization. Data stored in Key Vault is encrypted using the Advanced Encryption Standard (AES) with 256-bit keys. Data is also digitally signed with the SHA-256 algorithm. This ensures that the data is authentic and has not been tampered with.
In addition to encryption, Key Vault also provides authentication and authorization mechanisms to protect data. Authentication requires a valid identity, such as a username and password, to access the data. Authorization allows an administrator to assign roles and permissions to users, ensuring that only authorized individuals can access specific data. One of the key benefits of Key Vault is its ability to securely store secrets in the cloud. Key Vault is integrated with Azure Active Directory (AD) and can leverage existing AD authentication and authorization policies.
Additionally, Key Vault can be configured to use hardware security modules (HSMs) to further protect data. HSMs are dedicated devices that provide physical security and are used to store cryptographic keys. Finally, Key Vault helps organizations meet compliance requirements by providing a secure, auditable platform for storing and managing keys. Key Vault provides detailed logs of all activity, allowing organizations to track who accessed which keys, when they were accessed, and what actions were taken.
This enables organizations to maintain compliance with regulations such as HIPAA and PCI DSS. Azure Key Vault provides organizations with a secure, cost-effective way to manage their secrets and meet compliance requirements. By leveraging encryption, authentication, and authorization, organizations can protect their data from malicious actors and ensure that only authorized individuals have access to it. Additionally, Key Vault helps organizations meet compliance requirements by providing detailed audit logs and the ability to use HSMs for additional security.
What to Consider When Evaluating Key Vault Security
When evaluating the security of a Key Vault, there are several important considerations to keep in mind. First, it is important to assess the security features of the Key Vault itself. It is essential to understand the authentication and authorization mechanisms used to protect access to the vault, as well as the encryption and key management protocols in place. Additionally, it is important to ensure that the Key Vault has adequate logging and monitoring capabilities in order to detect and prevent any malicious activity. Second, it is important to consider the policies and procedures used to protect the data stored in the Key Vault.
This includes both physical and digital security measures, such as the use of firewalls, intrusion detection systems, and other security measures. Additionally, procedures should be in place to ensure that keys and credentials are securely stored and rotated regularly, as well as access restricted to only authorized personnel. Finally, it is important to evaluate the overall security posture of the organization responsible for managing the Key Vault.
This includes assessing the organization’s ability to respond to potential security incidents, as well as its commitment to implementing best practices in data security. These are just a few of the considerations to keep in mind when evaluating the security of a Key Vault. By assessing the security features of the vault itself, the security policies and procedures in place, and the security posture of the organization responsible for managing the Key Vault, organizations can ensure that their data is properly protected.
A Comprehensive Guide to Implementing Azure Key Vault
Introduction Azure Key Vault is a cloud-based service that helps securely store and manage cryptographic keys, secrets, and certificates. It allows users to store keys and secrets in a secure, centralized location and easily access them from anywhere. With Azure Key Vault, businesses can protect their data and improve their security posture. This comprehensive guide will cover the process of implementing Azure Key Vault, from setting up the service to managing the security of the vault. Creating an Azure Key Vault The first step in implementing Key Vault is to create a vault in the Azure portal. To do this, navigate to the “Create a resource” page in the portal and search for “Key Vault.” Once you select Key Vault, you will be prompted to enter a few details, such as the name of the vault, the resource group, the subscription, and the region.
Once you have entered the details, click “Create” to create the vault. Configuring Access Policies Once the vault is created, it is important to configure the access policies. Access policies control who has access to the vault and what they can do with it. To configure access policies, go to the Key Vault resource and select “Access policies.” From here, you can add users or groups to the vault and specify what type of access they have. Setting Up Secrets Once the access policies are configured, the next step is to set up secrets. Secrets are pieces of sensitive information, such as passwords, API keys, and certificates.
To set up secrets in the vault, select the “Secrets” option in the vault. From here, you can upload new secrets or generate them. You can also set up expiration dates and manage the permissions for each secret. Creating Keys The next step is to create keys in the vault. Keys are used to encrypt and decrypt data. To create keys, select the “Keys” option in the vault. From here, you can create symmetric or asymmetric keys and manage their permissions. Managing Certificates The final step is to manage certificates in the vault. Certificates are used to authenticate and establish secure connections.
To manage certificates, select the “Certificates” option in the vault. From here, you can upload certificates, manage their permissions, and set up renewal policies. Conclusion Azure Key Vault is a powerful service that helps businesses securely store and manage cryptographic keys, secrets, and certificates. This comprehensive guide has covered the process of implementing Azure Key Vault, from setting up the service to managing the security of the vault. By following the steps outlined above, businesses can create a secure environment to store their data and ensure their security posture is strong.
A Deep Dive into the Security Features of Azure Key Vault
Microsoft Azure Key Vault is an important component of the Microsoft Azure cloud computing platform. It provides a secure and compliant environment for managing and storing cryptographic keys and secrets such as passwords, certificates, and connection strings. This article provides a deep dive into the security features that Azure Key Vault provides. Azure Key Vault is designed to meet stringent security requirements and provides a number of features to help organizations protect their cryptographic keys and secrets. Key Vault uses industry-standard encryption algorithms to protect data, and is compliant with a number of security and privacy standards, including ISO 27001, PCI DSS, and HIPAA.
Azure Key Vault also provides access control to ensure that only authorized individuals can access the keys and secrets stored in the vault. Access can be granted to users, applications, or services based on their assigned roles. Access control is enforced by using Azure Active Directory (Azure AD) and identities are authenticated using Multi-Factor Authentication (MFA). Azure Key Vault also provides audit logging to help organizations track who has accessed the vault and what changes have been made. Log entries include user identity, time of access, and type of access.
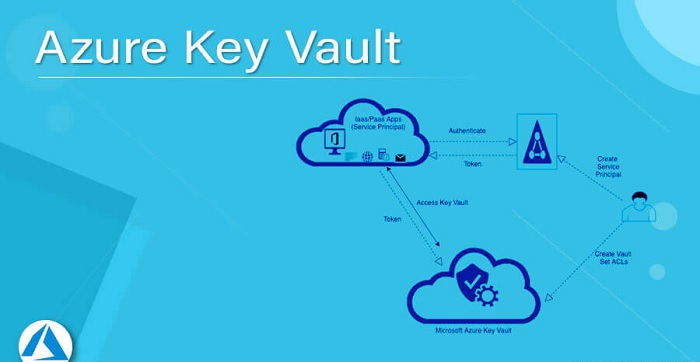
Audit logs are stored in a secure storage account and are encrypted using the encryption keys stored in Azure Key Vault. Azure Key Vault also provides threat detection and alerting features to help organizations detect and respond to potential security threats. The vault can be configured to alert administrators when there is an abnormal or suspicious activity. Finally, Azure Key Vault also provides a secure backup and restore feature that allows organizations to easily back up and restore their keys and secrets in the event of a disaster. Backups can be stored in an external storage location or in a secure cloud storage account.
Azure Key Vault provides a secure and compliant environment for managing and storing cryptographic keys and secrets. It provides a number of security features to help organizations protect their data and ensure that only authorized individuals can access the keys and secrets stored in the vault. It also provides audit logging, threat detection, and alerting features to help organizations detect potential security issues. Finally, it provides a secure backup and restore feature to ensure that the keys and secrets stored in the vault can be recovered in the event of a disaster.
Best Practices for Securing Your Data with Azure Key Vault
1. Implement Multi-Factor Authentication: Multi-Factor Authentication (MFA) adds an extra layer of security to Azure Key Vault. MFA requires users to provide multiple forms of authentication, such as a password, PIN, or biometric, to access the vault.
2. Use Role-Based Access Control: To ensure that only authorized personnel have access to your data, use Role-Based Access Control (RBAC) to assign permissions to different users. RBAC allows you to specify which users can access specific resources in your Key Vault.
3. Create and Manage Service Principals: Service Principals are service accounts that can be used to access Azure resources. To create and manage Service Principals, use the Azure Active Directory service.
4. Use Azure Active Directory Applications: Azure Active Directory Applications allow you to control access to your data. You can use these applications to define which users and applications have access to your Key Vault.
5. Use Encryption and Key Management: Encryption and key management are essential for securing data stored in Azure Key Vault. Use encryption algorithms to protect data stored in the vault, and use key management to control access to encryption keys.
6. Monitor Your Key Vault Activity: Monitoring your Key Vault activity can help you identify any suspicious activity or potential security threats. Use Azure Monitor to monitor your Key Vault activity and take appropriate action.
7. Implement Data Protection Policies: You can also implement data protection policies to ensure that data stored in Azure Key Vault is secure. These policies should include guidelines for data access, encryption, and other security measures.
8. Back Up Your Data: Lastly, you should back up your data stored in Azure Key Vault. This will ensure that your data is safe in the event of an emergency or system failure.
Final Thought!
Azure Key Vault is a secure and reliable way to store and manage sensitive information for your organization. It is designed with industry-standard security protocols and provides comprehensive monitoring and auditing capabilities to ensure the safety of your data. With Azure Key Vault, you can rest assured that your data is secure and always available when you need it.
Comments (0)